How to deliver PFX certificate with Intune
This article provides step-by-step instructions for importing a PFX certificate into Microsoft Intune.
Table of contents
- Overview
- Here's how to install a PFX certificate to Microsoft Intune.
- PFXImport
- Build PFXImport
- A dedicated machine for Certificate Connector
- AAD App registration for PFXImport
- Certificate import
- Endpoint Manager Portal configurations
- How to check you delivered the certificate on the end devices
- Troubleshooting
Overview
A brief overview of standard
PKCS (Public Key Cryptography Standards) is a set of standards and specifications developed by RSA Laboratories for secure data transmission using public key cryptography. PFX (Personal Information Exchange) is a file format that uses the PKCS #12 standard, which supports the safe storage of certificates, private keys, and all certificates in a certification path.
Intune
If you manage your devices with Microsoft Intune, you can use an imported public-key cryptography standards (PKCS) certificate configuration profile to deliver the same certificate across all your devices. This is the most straightforward approach you can find in Intune for certificate delivery.
Workflow
In the PKCS certificate deployment process in Intune, an admin creates a PKCS certificate profile, and Intune works with the on-premises Intune Certificate Connector and Microsoft Certification Authority to issue, encrypt, and send the PFX User Certificate to the device, which then reports the certificate status back to Intune.
Here's how to install a PFX certificate to Microsoft Intune.
To start, you must have or create a self-signed PFX certificate with a password-protected private key. You can do this, for example, using the Windows Server Certificate Authority or PowerShell.
Create the simplest self-signed exportable certificate with PowerShell (admin mode)
New-SelfSignedCertificate -CertStoreLocation "cert:\CurrentUser\My" -Subject "CN=MyCertTestDemo" -KeyExportPolicy Exportable -KeyLength 2048
Export-Certificate -Cert cert:\CurrentUser\My\[THUMBPRINT_FROM_FIRST_CMD] -FilePath c:\publicKey.cer
$mypwd = ConvertTo-SecureString -String "1234" -Force -AsPlainText
Get-ChildItem -Path cert:\CurrentUser\My\[THUMBPRINT_FROM_FIRST_CMD] | Export-PfxCertificate -FilePath C:\privateKey.pfx -Password $mypwd
PFXImport
The PFXImport PowerShell Project is a tool that helps you import PFX certificates to Microsoft Intune. The PFXImport PowerShell Project provides you with cmdlets to do the operations easily. The biggest problem with this cmdlet is that it's only available as a source code, so you must build it yourself on your local machine. You should build the PFXImport PowerShell Project cmdlets yourself using Visual Studio. You must download from GitHub and build the PFXImport project with Visual Studio.
Build PFXImport
Download Visual Studio 2022.
Download PFXImport Powershell Project from GitHub.
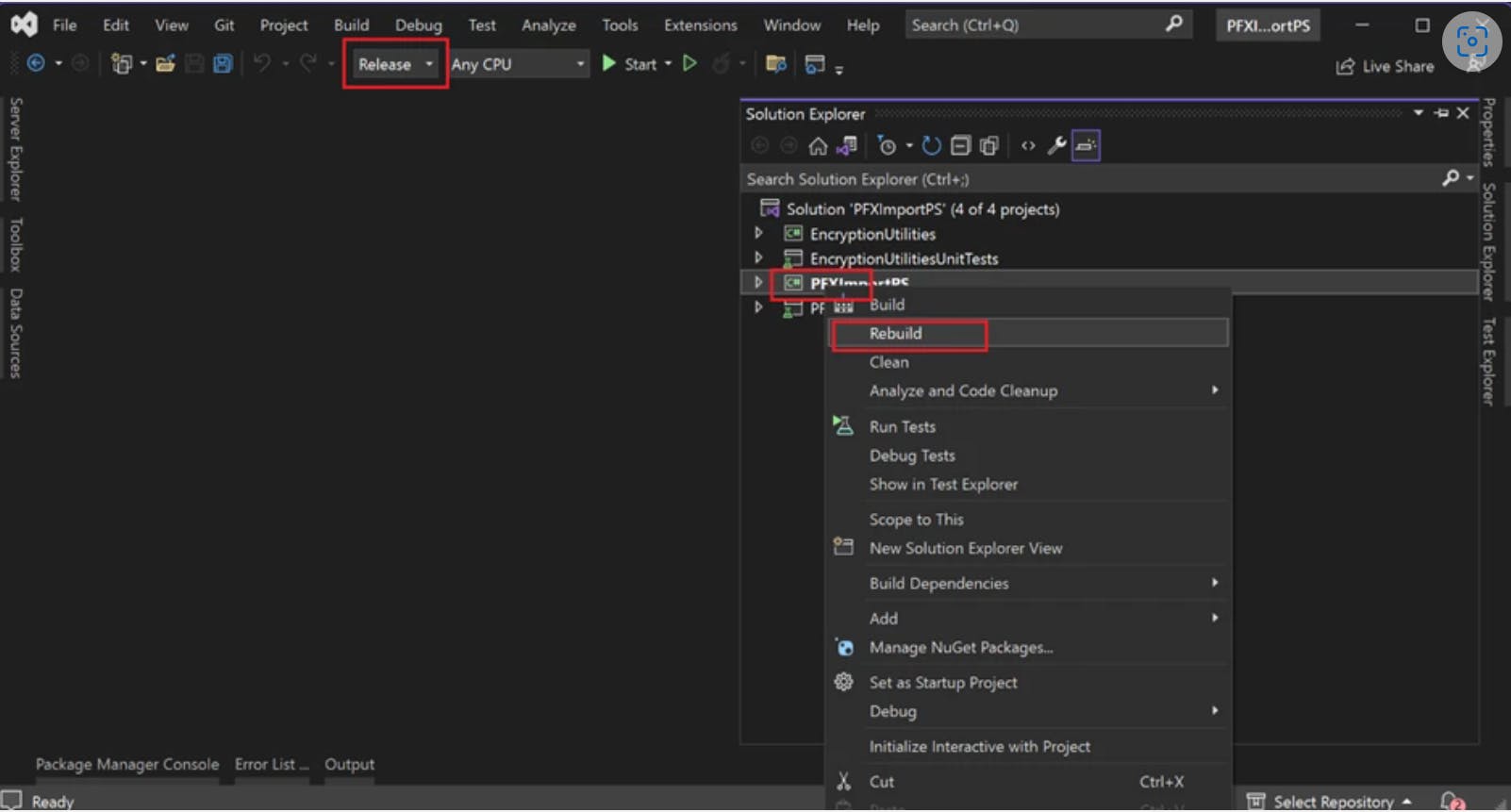
Open PFXImportPS.sln file, switch it to release mode and build the project.
A dedicated machine for Certificate Connector
After building the PFXImport project, you must set up a dedicated machine for the Certificate Connector. This machine will be responsible for distributing the PFX certificate to Intune, which will then be distributed to the end devices. Once the machine is set up, you must download the IntuneCertificateConnector.exe file and run it on the designated Certificate Connector machine.
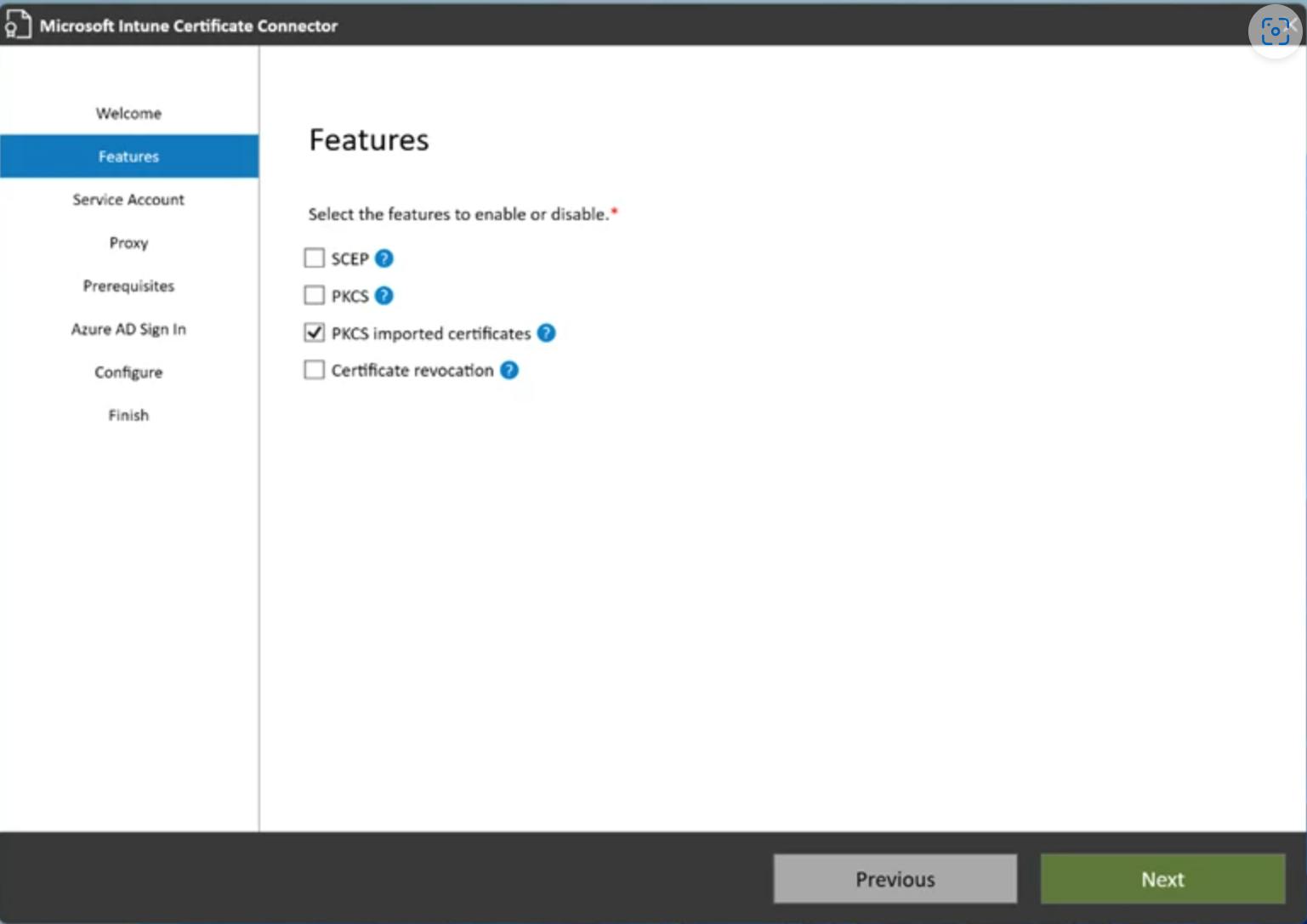
During installation, be sure to select the PKCS imported certificates checkbox.
AAD App registration for PFXImport
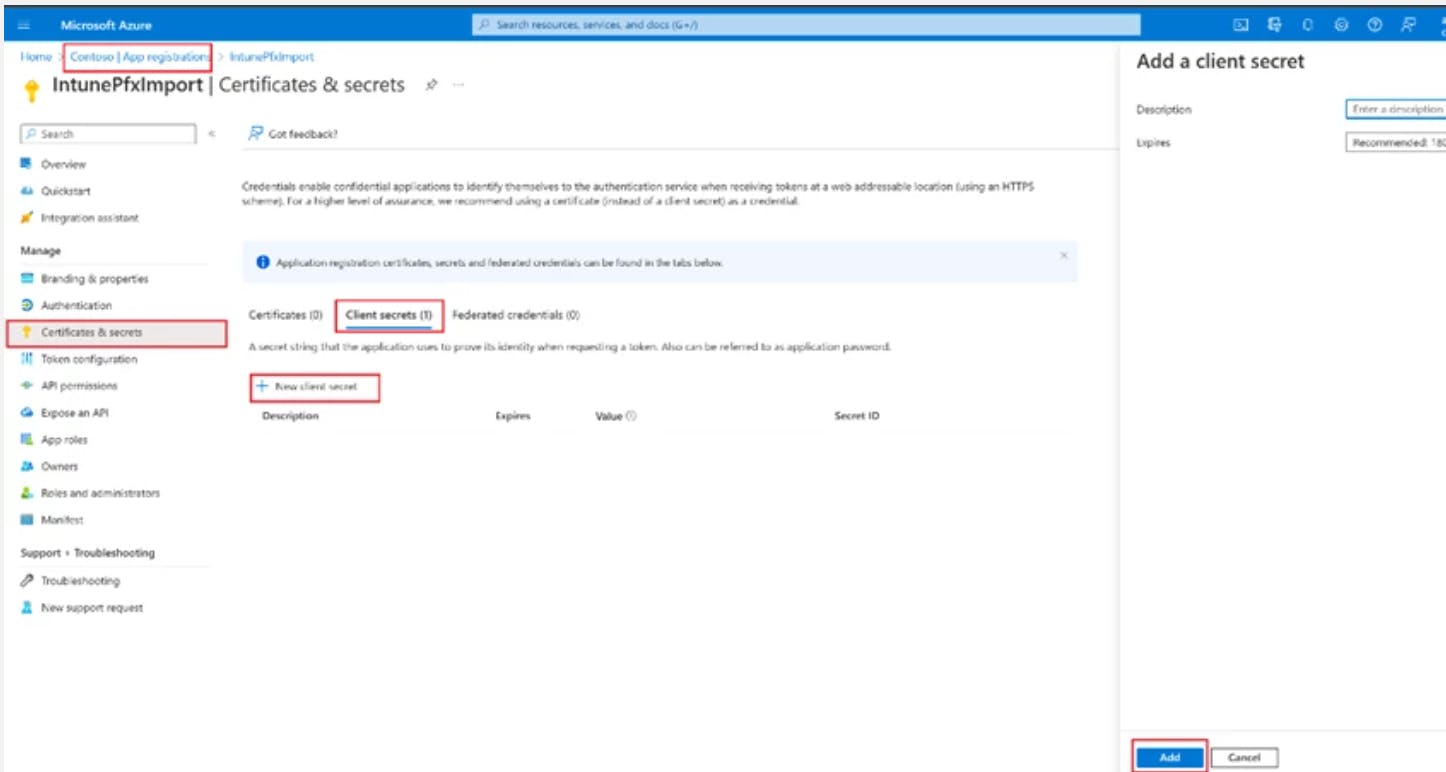
Next, you must grant the cmdlet access to Azure AD, which requires creating an application registration in Azure AD.
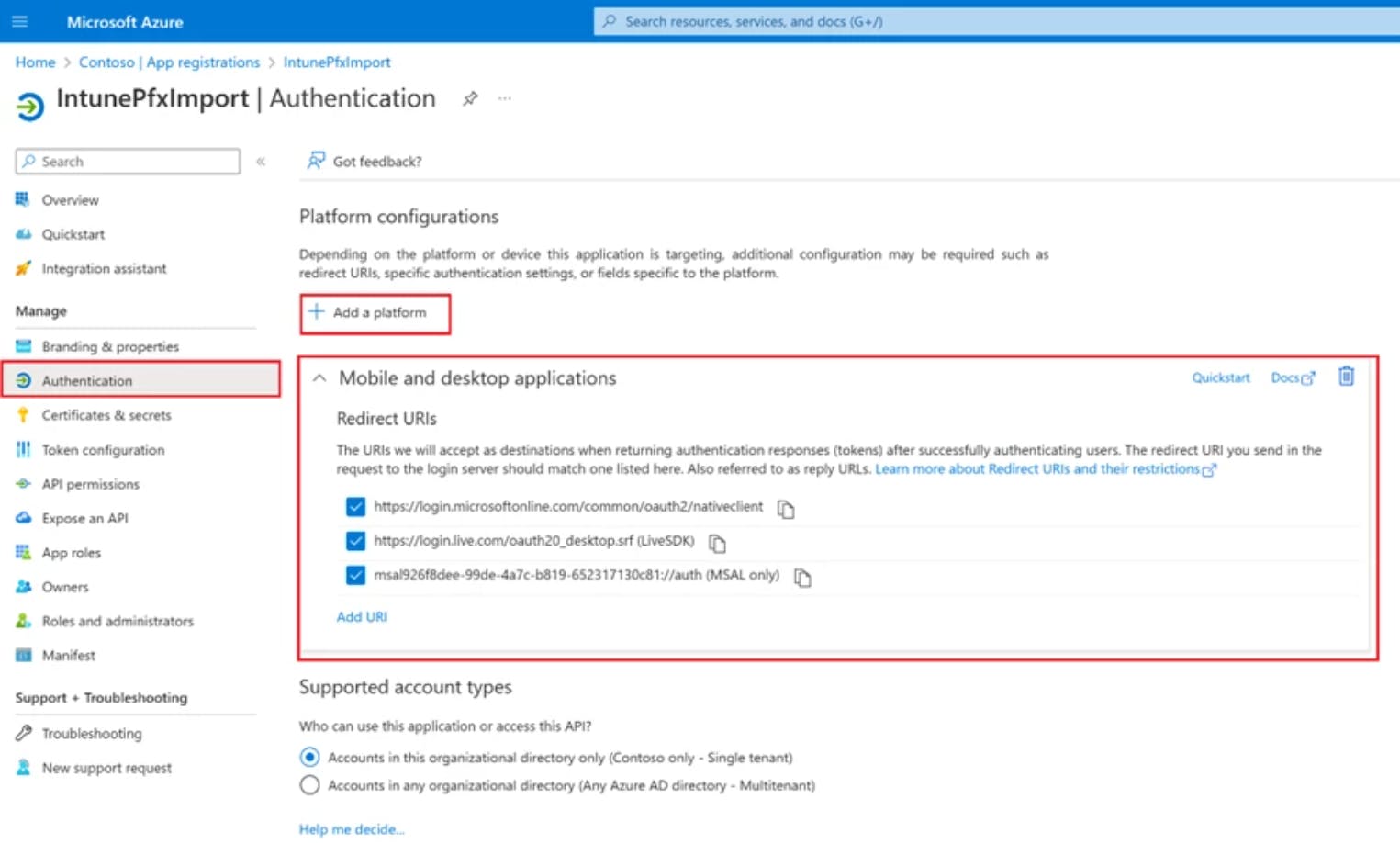
Start up the designated machine and carry out all subsequent actions on it.
Then copy your self-signed PXF certificate to the Certificate Connector machine.
Copy the project binaries to the machine. (~\Intune-Resource-Access-develop\src\PFXImportPowershell\PFXImportPS\bin\Release).
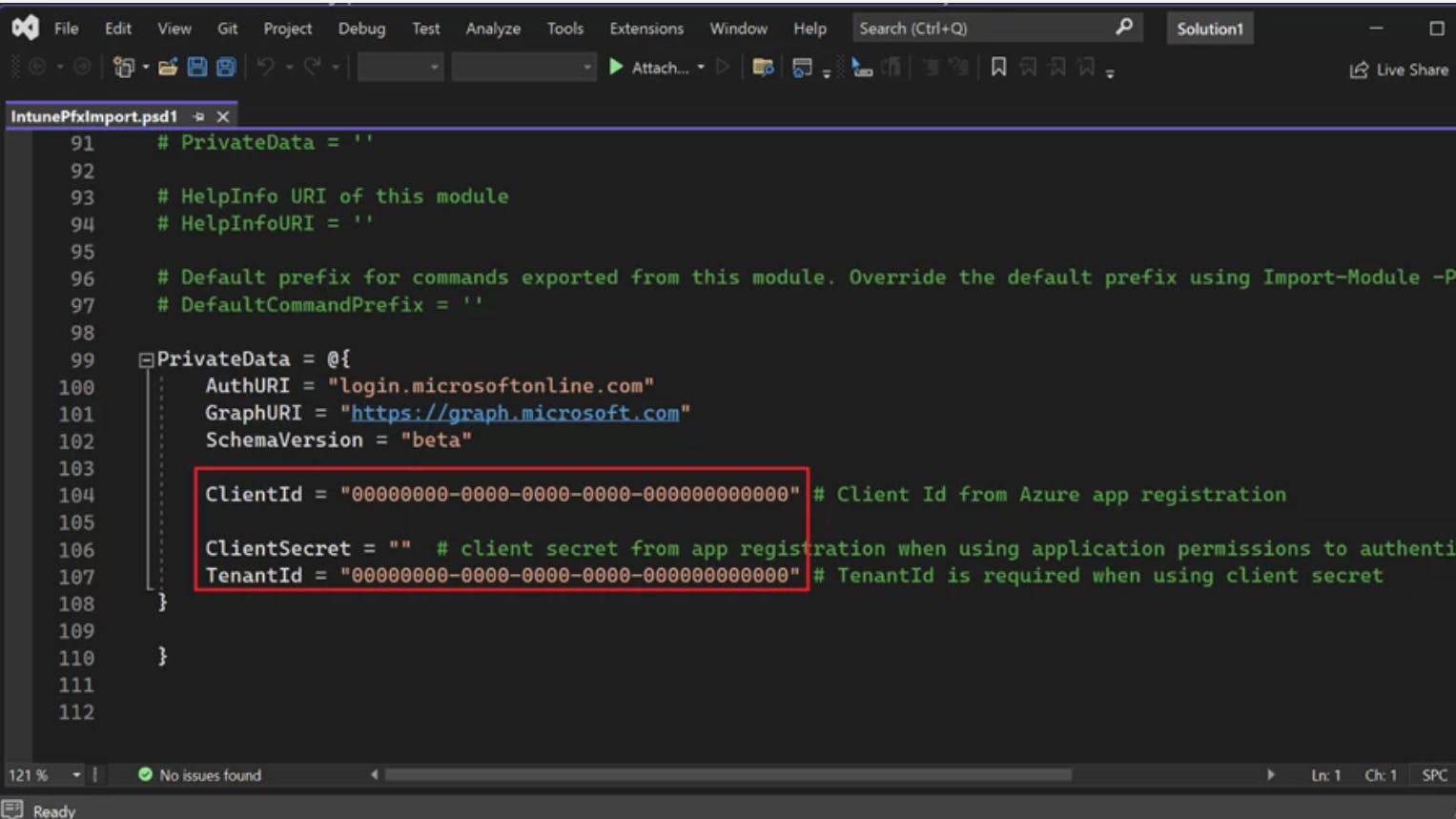
Modify IntunePfxImport.psd1 in the Release folder with data from App registration.
Certificate import
Once the Certificate Connector is installed and the app registration for PFXImport is configured, you can now import the PFX certificate into it. To do this, run PowerShell Terminal as an administrator and use the PFXImport cmdlets to import the PFX certificate into the Certificate Connector.
Import-Module .\IntunePfxImport.psd1
Set-IntuneAuthenticationToken -AdminUserName “<ADMIN@DOMAIN.COM>“
Add-IntuneKspKey -ProviderName “Microsoft Software Key Storage Provider” -KeyName “PFXEncryptionKey”
$SecureFilePassword = ConvertTo-SecureString -String “<PFX CERTIFICATE PASSWORD>” -AsPlainText -Force
$UserPFXObject = New-IntuneUserPfxCertificate -PathToPfxFile “C:\<SOME PATH>\<PFX CERTIFICATE FILENAME>.pfx” $SecureFilePassword “<END_USER@DOMAIN.COM>” “Microsoft Software Key Storage Provider” “PFXEncryptionKey” “smimeEncryption”
Import-IntuneUserPfxCertificate -CertificateList $UserPFXObject
To deliver the certificate for additional end users, repeat steps 5 and 6 while including their logins. Use the following command to validate the result.
Get-IntuneUserPfxCertificate -UserList “<END_USER@DOMAIN.COM>”
Once imported, the PFX certificate will be distributed to all devices managed by Microsoft Intune.
Endpoint Manager Portal configurations
Navigate to the Device tab, select the desired operating system, and click the "Create profile" button.
Choose "PKCS imported certificate" as the profile type (for Android, also select the "Android Enterprise platform" option).
Provide a name and description for the profile.
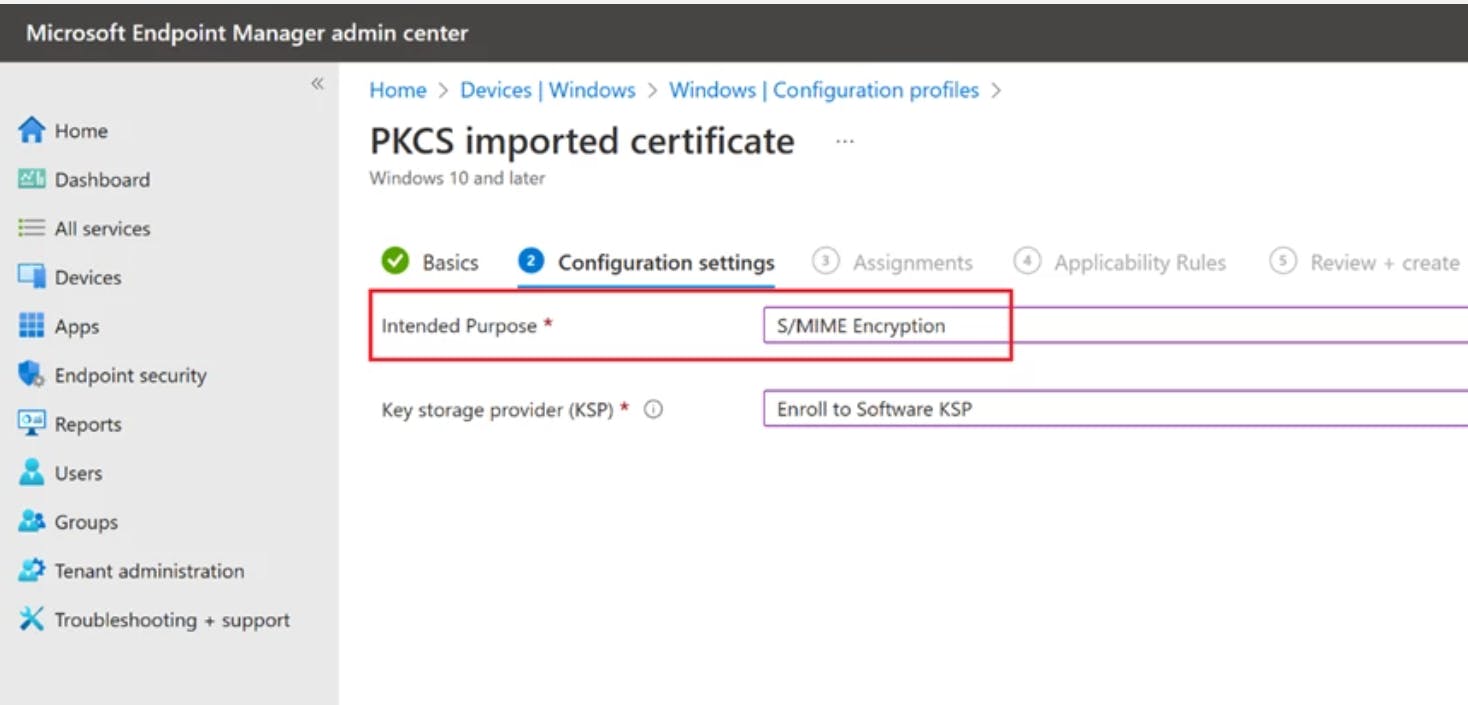
Select "S/MIME Encryption" as the "Intended purpose."
Complete the process by assigning the profile to a user group (for Windows, also select the "Enroll to Software KSP" option).
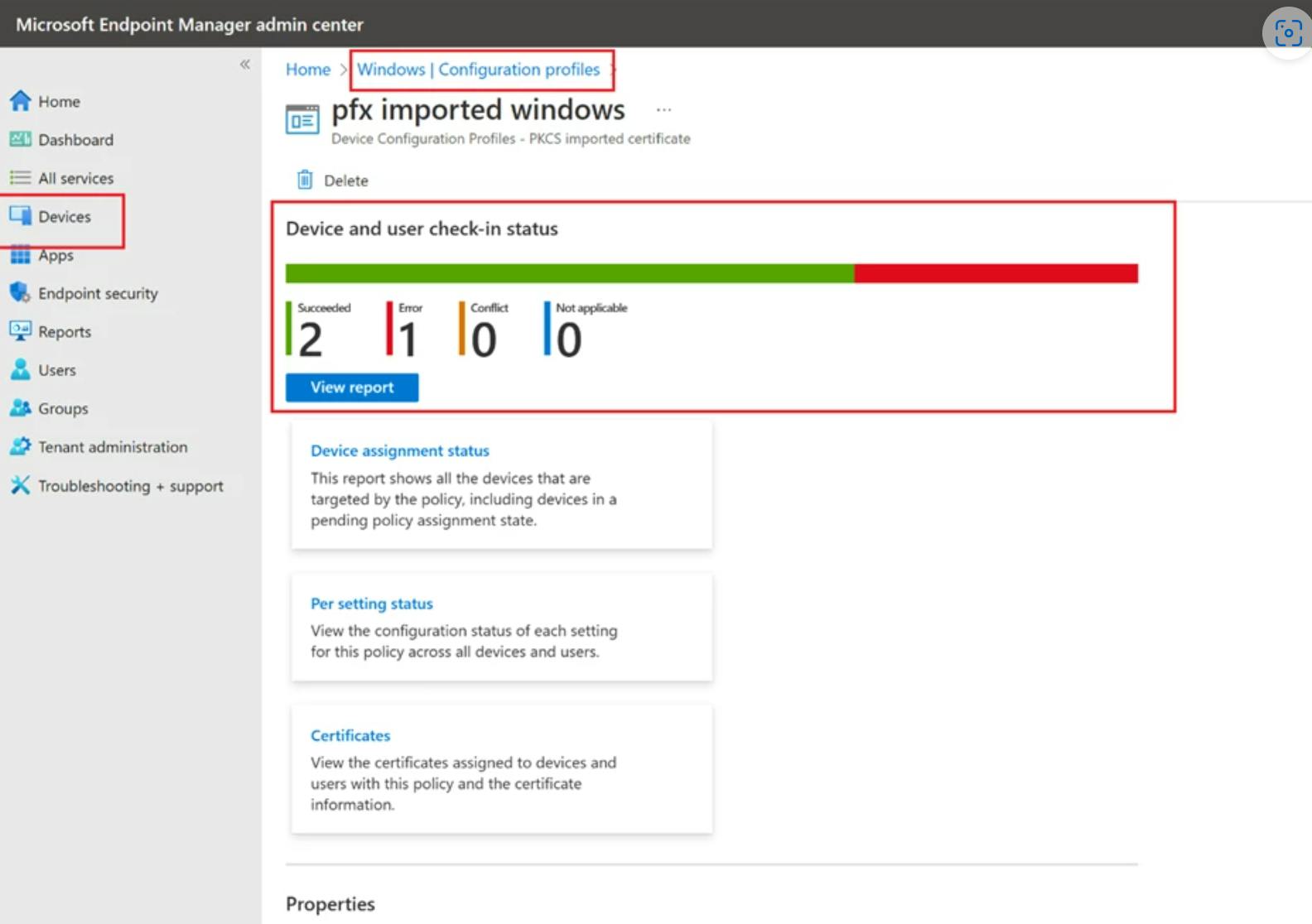
Verify the configuration on the profile details page.
How to check you delivered the certificate on the end devices
All your devices are expected to be registered; you can do so using the Intune Company Portal app.
On Windows:
You can run the following command Certmgr.msc
On Android
You can view an app like My certificates installed certificates on Android. Please note, this app needs to be installed in the same work profile to access certificates distributed from Intune.
On iPhone
You can find the certificate under your organization's Management profile. General -> VPN & Devices Management -> Management Profile -> More Details
Troubleshooting
One way to troubleshoot is to use Windows Event Viewer to review the Certificate Connector logs. You can find more information at the following link.
In conclusion, I hope this article has provided more clarity than confusion. Please follow me for exciting future reads.
